Security at Waydev
Security is one of the biggest considerations in everything we do.
Security is our top priority.
Check our information about Security at Waydev:
About Security at Waydev
The entire Waydev team is focused on keeping you and your data safe. We adhere to industry-leading standards to manage our network, secure our application, and set policies across our organization.
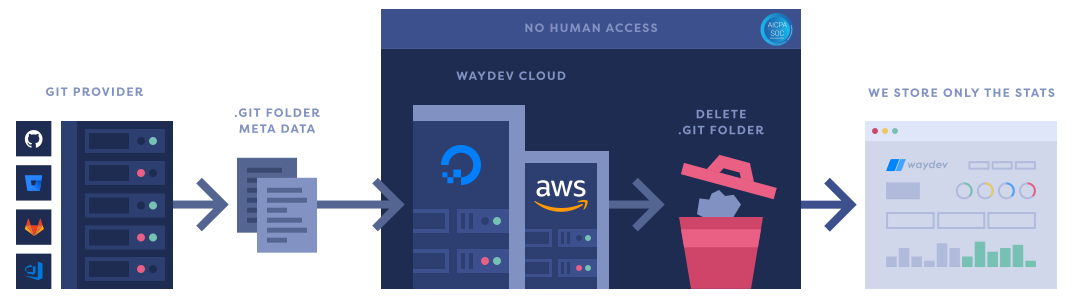
Your security is critical to us. We do not keep any copies of your repositories, we only copy the ".git" folder (metadata), and right after our analysis is complete, we delete it in real-time.
We download a bare clone of your repositories using that token. A bare clone involves downloading only the diffs and does not check out a working tree.
Eventually, these stats get written to our database. No code is persisted at any point in the process. The service that initially cloned your repositories gets its container destroyed.
We are also SOC 3 compliant (highest level of trust and transparency):
The compliance report attests that our controls and procedures are in place, and operating effectively.
As a cloud service provider, our controls and processes demand the highest level of trust and transparency. Waydev’s information, security practices, policies, and procedures are suitable to meet the SOC 3 trust principles criteria for security, availability, and confidentiality. Waydev has the highest level of security measurements against any potential security breach.
We always connect via your Git provider tokens: When you disconnect your repositories, all associated stats are purged from the system.
This can be accomplished securely by allowing public access via your Git provider token to internal repositories.
This ensures that all data transmitted to Waydev is done over a secure protocol, and allows our customers to maintain strict authentication and access security using Git provider tokens.
Waydev does not store your git credentials:
Our code only interacts with GitHub, GitLab, BitBucket, Azure DevOps, Jira, and Gerrit, using temporary token credentials that we refresh frequently.
All data is transmitted using a secure protocol:
Our code only interacts with Git providers using temporary token credentials that we refresh frequently. We use industry-standard 256-bit SSL (HTTPS) encryption for all internet-facing traffic to secure your data in transit.
We use Stripe (www.stripe.com) for all credit card and payment information processing. Stripe has been audited by a PCI-certified auditor and is certified to PCI Service Provider Level. This is the most stringent level of certification available in the payments industry.
Highly Secure Payments: We use Stripe for all credit card and payment information processing.
Stripe has been audited by a PCI-certified auditor and is certified to PCI Service Provider Level. This is the most stringent level of certification available in the payments industry.
All card numbers are encrypted at rest with AES-256. Decryption keys are stored on separate machines. None of Stripe’s internal servers and daemons are able to obtain plaintext card numbers; instead, they can just request that cards be sent to a service provider on a static whitelist. Stripe’s infrastructure for storing, decrypting, and transmitting card numbers runs in separate hosting infrastructure and doesn’t share any credentials with Stripe’s primary services (API, website, etc.).
Updated 6 months ago